Introduction
At McAiden, our commitment to cybersecurity leads us to engage in rigorous vulnerability research and security assessments. In the course of these activities, we might identify security vulnerabilities within both proprietary and open-source software products. Recognizing the critical importance of these findings, we aim to responsibly share relevant information with the affected product vendors, our clientele, and the broader cybersecurity community. Our primary objective is to mitigate the risks associated with the disclosure of such vulnerabilities, ensuring that they are addressed in a manner that minimally impacts the involved parties. This Responsible Disclosure Policy outlines the essential procedures and timelines that are to be adhered to for the effective resolution of identified security concerns prior to any public dissemination of information.
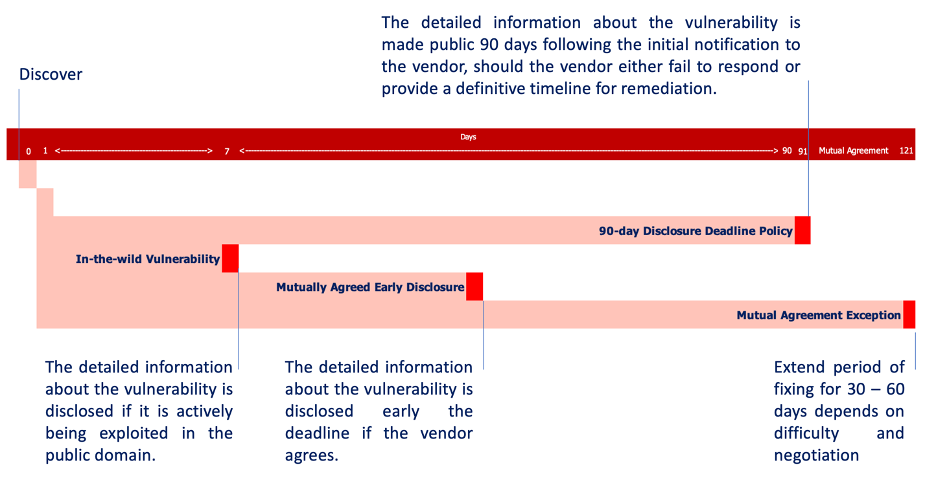
90-day Disclosure Deadline Policy
In alignment with industry best practices, notably adopted by leading entities such as Google, McAiden enforces a 90-day disclosure timeline. This policy stipulates that upon notification of a security vulnerability by McAiden, vendors are granted a period of 90 days to develop and deploy a remedial patch for their users. Subsequent to the availability of the patch, McAiden reserves the right to publicly disclose the details of the vulnerability.
For instance, should a vendor address a reported security flaw on the 47th day following our notification, McAiden would proceed to publicly share the vulnerability specifics no earlier than the 48th day. Conversely, in scenarios where a vendor fails to remediate the identified issue within the stipulated 90-day window, McAiden will proceed with a public disclosure upon the lapse of this period.
In-the-wild vulnerabilities
Our policy adapts in situations where there is concrete evidence to suggest that a vulnerability is actively being exploited against users in real-world scenarios. In such cases, the standard 90-day disclosure framework is substituted with an expedited 7-day disclosure protocol to promptly address the imminent threat posed by the exploitation of the vulnerability.
Mutually Agreed Early Disclosure
McAiden acknowledges that certain circumstances may warrant an earlier disclosure of vulnerability details than what is outlined in our standard policies. In such cases, McAiden is open to reaching a mutual agreement with the concerned vendor to advance the disclosure timeline. This approach is contingent on a collaborative discussion between McAiden and the vendor, ensuring that any early disclosure is executed with due consideration for the potential implications.
Mutual Agreement Exception
At any point, if the vendor is actively working on a fix but requires more time, McAiden and the vendor can mutually agree to extend the disclosure deadline. Such an extension would be based on transparent communication about the efforts being made to address the issue and a reasonable timeline for the fix. Typically, extension periods might range from an additional 30 to 60 days, but they can be shorter or longer based on the specific circumstances and the negotiations between McAiden and the vendor.
The following key is McAiden Research Lab’s PGP public key (mrl@mcaiden.com):
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQINBGeQwQMBEAC5muUEKa5+D6y7yYX5A1DFuSbs94y15w1f9TqZ0N8pwuY2vxRb
JQo3PTg7neRwtNwH6pmTEWrx/F+qissAfHaI9KokpmXl70FEFBkMJtRCRpOGt+Nx
x4MO565gXsxwhZbxhjgGBjUztsGr9opTObsHFoUzoS1Y/rQbUZtvRDmmerinVaDc
0jqjSt7U4fc/9zL75opdMO0ma2k7sC0Rt3V+qXRA9DXklcAoEYv1F/sIRlF+yJOj
Cq6Py4CvbyKlolCnS7U5+JRvoEozYey7pyyvFOJaRuZK+0+ssQHkDm73BCC7AAfI
fzbE7QjDRWsSLjp/8eI6WaBFfyl6NaWxuJzJ91ZMp2MPUgqoRZr/daccazyZ7rLS
uqdFLdguobkHe0jEooF38LSUVl/YyGupSlVXNVJV213wFsgEi2igR1P1/5ILSIfn
aZKopl5MP+DVCR+pY1hjK+DH6GuvkHBjstAIlFsYCQ2uQaHD0RKB6URQZzI2mWhN
rGc/hfp0aS0xljUKzMrgu+z1+geZSrgDs2PqNlemBfZsLI7NBk0R6/IEDnC5qRUx
h+JGo30keR86k+x04lAV8AFd5OCFU0xz382QrnSyWM4Hin2T8UwlSYYS1qEb+HqV
fQ/vFhZFoFvNeF6HHcsfoolQUW+oWVz/kUTOsdR6+MBbOoQO81tEtZbfnwARAQAB
tCZNY0FpZGVuIFJlc2VhcmNoIExhYiA8bXJsQG1jYWlkZW4uY29tPokCVwQTAQgA
QRYhBHEpCPGw7f2akaFFfRm9tncJiEuSBQJnkMEDAhsDBQkFo5qABQsJCAcCAiIC
BhUKCQgLAgQWAgMBAh4HAheAAAoJEBm9tncJiEuSRK0P/0pWBhUrEl0bINAZw5OZ
ewhrpFtWh++OUBwhD37i60YdeWMzdsDgQKZcDV07dYgr88R5+My9VirN34KlkVWF
wSvv/lWqCdw+duNX6zwYUrSFw2IDVsyxirboJD9Z5NJG7L6X3qrnyNJEGPwhJdlx
vNYSwTXDvqx/sFab+d379YVeg9hoqO7kZ9+/jg8oOI0ybPj70JSFekAZuG0WqHwC
NmjQZYkTW6RN58sWaPgFgc1dhKh+ckXOMrBz0QUYEyLyyHnMz3doTBI/KEJ4CDRc
StR3NFdrrIiUDWCZKP1l4Bxg09raIUVdmkgiGax4au0/aW27yEL64DqLoCrV/0gG
5wA/8bNg9EJvHWr3f4Uz6ArUsH1dQZYxIUw0R/ZmmWK/6eWbUY+HX2kxUWgOAbT7
3Z/vfouQMmQz6iOIcJDyzN3VBpnbuOkPm4IqbT4ieO0aB9HNgog3GJE65VgixSTE
Dksk4UnpGl/KyD6mowQWyGYM3uMkptfcCFn6cx6kJx2dmqV+pN3qgfIP9wvlNwQ5
LyqH4hoqqqCSkyRcLH2gX2Y+vMy8z7WR22yJpEUOr3flHeoozCMk+1BTVh/5jw6K
okuiwKo4PobWtu7lQxp7AtMECqk7shZRpi1h1uZScX3MMzR4eWikxiO6AzFEVbZj
2jc2NCyOGH1w5u5W0GNG774AmQINBGgq6wwBEAC37Uk+WMt/H5beRwGTtimKOhwp
BAWJPmVxlAaUX3YL816692LG+1TUhTz2TvlRisbhp3RWWENgyLJFxsW+Gn7kesuP
ll9OFHXzfWBby44wQz7VEyjAV+MYIrWn9yO5M7P2Jmcy+5va4qeob7miLQGQVB9L
76YY7/p7XzGAfJA6OqtN14QA2j3w0cKXfr7mYIHIKCmitX/K2AyxP9eR81StyPJI
KjJqpErZ6X2hHd86CsMPc1jeq3feUFM5ejXJWG7uygU0T4YtX98eHzuR5rZ3rLbc
8n8zSHQ/8l5I8O3IxYzknb2xtcV0dvHrj+m9RK4reop+4WSDGQeijfly+GcuDmFv
IvCtFLMlod1zbzQ8WAI6nE1+f/V+icDsgtyCcmCk+SQB3xnGyJ+NHDveCmS9DTnY
rDNIW9JmlfROFTFVdeFZfqYUS8947I+BdZSA5Ww5rYgvUUgFBVvXw2HQyc+eooRe
mjA+B1s2EJPl6867owZda//PGjxFfwxG6BCD/PiTMpxYafY1NDZ0zIP3S9ltQ6gF
wih82pB9WFBxtwZrVoF6qYr2PHZJhjYWa/c9x11QwdK/A8B9ScbTZPVrp+Q7resW
aIeeeAAZU6EpkcVtc/Cto05vS/ItvbS/WBXVIi65p9CkwqFwgph7V6ZYRh2ad7I7
LYy7LW8Rw2EfXuWNyQARAQABtCZNY0FpZGVuIFJlc2VhcmNoIExhYiA8bXJsQG1j
YWlkZW4uY29tPokCVwQTAQgAQRYhBK/w8wb0Y0V1yOiBb+ONLEszxC8pBQJoKusM
AhsDBQkFo5qABQsJCAcCAiICBhUKCQgLAgQWAgMBAh4HAheAAAoJEOONLEszxC8p
lacP/3OadBbfl536w2tdtKjnx7hw0fAc9MeytfmuKj6DlJr5gLFtLZ2344S4WAmP
OQwMU1Bq/IuLBH/k68bRP/a0C1pxZyKB73NiC2TgHhSKYlgXp5mNM0uO54w1Aj7o
SUdsFla9mmxwxbHDhvADhBosw15ROEC/CxtJlodgd9E+V+gSpWJmZVXndptVQy7h
qSE+ZgAq/8FdvzJKgFizhMVHWq9BD8wE6KquWk+yeR4V7pgAlhKL5kPrBocb8yPf
CMsy5CleMtCJWewbYzBWcJGhUrdUkIzPMFW846qFHEwARcHKIjqEzg7rsy7r7cot
X025XWo/H0Jqpxadrq6OhTq7dVlUfqCFAYbHiSTAc2iqqZGlqT6MyweUh1YdhzKW
sx04X10zywGt1a4J9ZgwxCy+ALsHRMocbve1XMltbwHZjiBaj8gFxlLkD1spGhqX
Ns4ODfiimHzKz12Vi5A4ScF7VIHkUd4GQt4RuC4D3EHuPfXzngGPh45Y7cYynUHt
EW3QMjIfgnU0vMOaoWUgy/MmLjkUGlWuZSTbhdNkkDi7uoeIjebMvZ8T+ybInod7
7Z5mMcVpQx9+UrSp+lZU+5AFr9IheXSf0GoVqeZYykr7+we7L4XyYvlyVFuAmnZU
xGdZ0wdjyM8gaLxNJoohci1qIg00wH2p4+GS/neeyYjouLPHuQINBGgq6wwBEADZ
Df0UmG+X/zJwz6ziFRpjSyUpDq7TXJyVGAkeEAXsyNIBRoTHPrflPZ1zWrcz6KQ1
8g7YIQqEm7xWxKWTxz9XkP6yX6YTAI7IBPRMt52w0CDlZo/T7WUwPL+An1CWvU4H
Ypf/pYFAAP8narIksvb7lQcbNEHB2Zaasl4YaaYYdyhHALLqcNGnUNU+Ee2wddTB
KvRLy+3jE/g0BnwQNJsXzhD8QHqnlIFpNA4zH/8aCrTIxmJQK4tPfQ0xjuBgn0GR
VIJc0B687RxZF3pjuYxey4U3i+cNl1oS3mQ3/aGrOGO2JOwRWzb76C+JLW8/tmaM
SIa3NkX5CtxH8jlDs4FsU6N6NkJywmsUXo/t4/9w4H33y33NLelkXbDrr8eDH2Iy
T9lLtV9RCJd/IZOGHf2jC4qi4fjL5a/th2/yght3+lxST1uKL916wO6Yjo9aSuQ1
SnkAa8L+pKrlkN3it+QZGkLeCgQwy+BXdBBPkybAb/Xi5yz4mLyYvtm+HR/Vc6JH
KD7YRxnhqkWGZMEpxZ8E3R2Wq5Uq866FvBDzmM/t1I7tCL8HzEreKS6Okvw21Nx1
LBEljMAYcKJuiwQiLU7u45R4/5jw2pRGa0JCcFq9OCAReH5snvW6S1chxPpY00sw
xV02yT165c/1luSLA1+Lw5XFLPMSJDLLTBqxE5mdcQARAQABiQI8BBgBCAAmFiEE
r/DzBvRjRXXI6IFv440sSzPELykFAmgq6wwCGwwFCQWjmoAACgkQ440sSzPELym1
dw//WHQgbTrcHfhASe0ijBSQ9/hu7MP0GDmpfZuu+sOOyPMrreNeZfoAmk2pBgSR
gtRnySiMNu/CAbHQeN7RzSGdpo85kVdTwuyfIGKfI+YuigEvDqgDZRux7mW5RurQ
5M9JR+Zu6FhA9k4DY90pGQfuBpk9CO+jz8+fsZflTRHNm/hSH4eOZq5Ik2gjd5Ll
JB39VPUQvJbMZBrntc3yIaipj0ek4y8Vq0WM6d4wT+/7AgfQXPwqeQ5HYQiGd5C0
6EOhQeqXy/njAV2lSheSEFigR7HC+uAqa3W1F3Dzadmh0ZBixHoiFE8WkvSbGofV
4NwB3kkz1BsFJO0OUNE8xa222196cIIC6k+CWfMzUNtzBktTtAOfbDb4IZ3VXgEI
T0vpEvlj9z1sfjnLvsHNlcQoL+xAdYP7TEgBI5BV6mjS0BYi4Hcj/6iEKjDYtfso
wlhL7VMxGsKKXBB7UqU6TD80PozT5r2CgJLVO9vbGOL/FkLQR+lvIrwrq/akXfJa
fUR2eobccbpn+JjexEY7Qc9Em0Qc3WrcsDTBYhGqLYsJtp15vEiolW/xs53s6V94
E4P7fPWKWuHdS8qnzLK5h9rlzuPTSe0ROXLzKhwqDbo7R8mjY9EnbELpAbXOfLrw
GM5AJiBMP6FxM8HxfjWWUcYslBGfmxuesXxiIhs5l7VxNhI=
=6fDk
-----END PGP PUBLIC KEY BLOCK-----


