| Title | Third-Party Keyboard Detection on Android |
| McAiden Vulnerability No. | MIDA2025-0001 |
| Product | Android |
| Found | 2025-01-20 |
| By | Nutthanon Thongcharoen (McAiden Consulting Co., Ltd.) Pumipat Korncharornpisuit (McAiden Consulting Co., Ltd.) McAiden Research Lab |
Vulnerability Overview/Description
Third-Party Keyboard Detection on Android
Third-party keyboards are gaining popularity on Android devices due to their enhanced aesthetics and functionality. However, they can also introduce significant security risks, particularly when developed by untrusted sources. Such keyboards may include malicious code capable of intercepting sensitive information typed by users, such as passwords or PINs.
In this article, we will describe about Third-Party keyboard by break the content into three parts:
Android Keyboard Setting
For the demonstration, I used a third-party keyboard application with the package name com.redraw.keyboard.theme.newkeyboard2018, which was installed on an Android emulator (Android Version 15).
You can download the application from the Play Store or, alternatively, obtain the APK file using the link provided below and install it using the ADB tool.
$ adb install 'Keyboard Pro 2024.apk'
Performing Streamed Install
Success
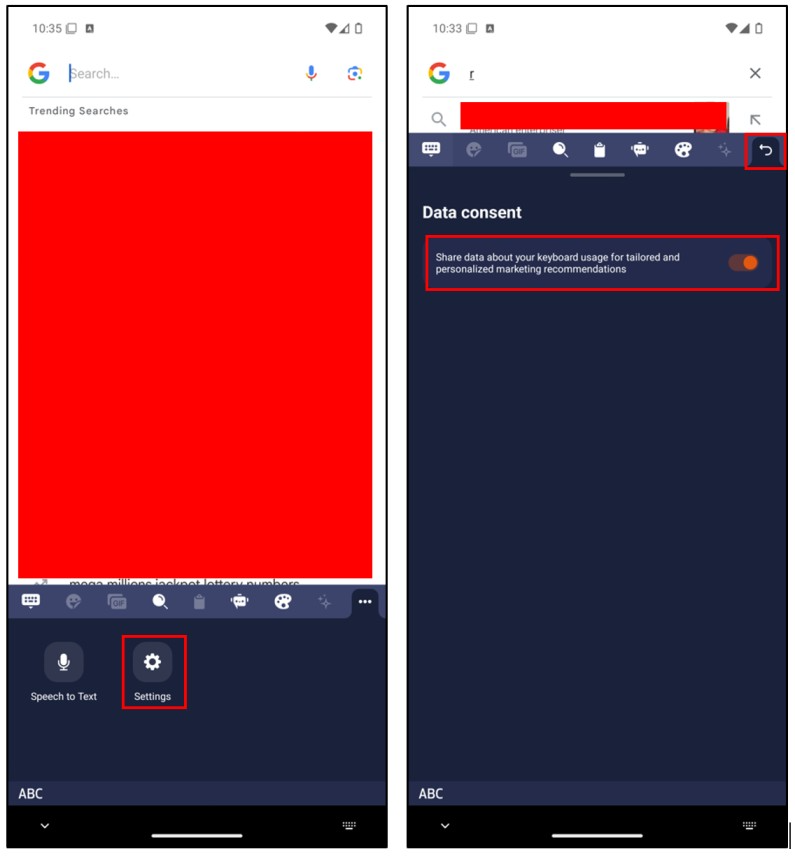
After installing the application and clicking “Get Started” button, a page titled Data Consent appeared, as shown below.
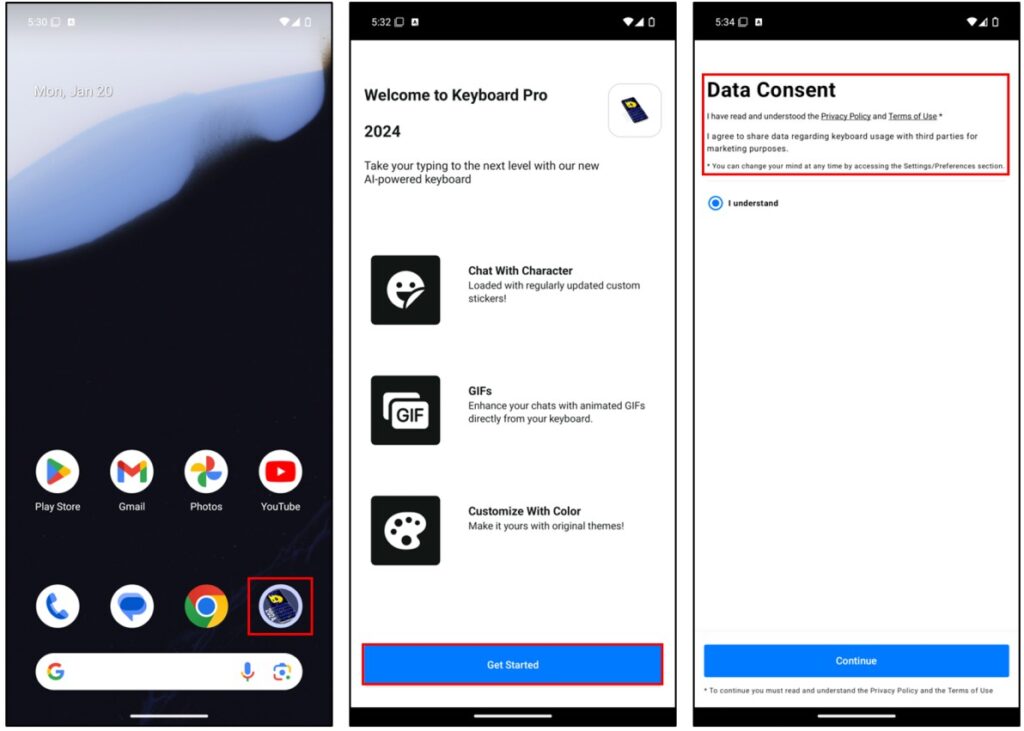
The application includes a Privacy Policy and Terms of Use, both of it can be accessed through the links provided:
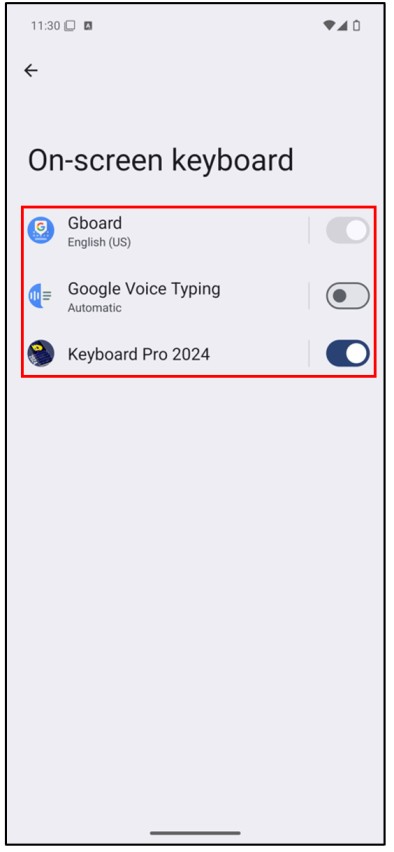
After tapping the “Continue” button, the application navigates to the setup process for configuring the keyboard on the Android system. In the first step, the keyboard is added to the list of available keyboards in the settings. In the second step, users are prompted to switch to “Keyboard Pro2024“
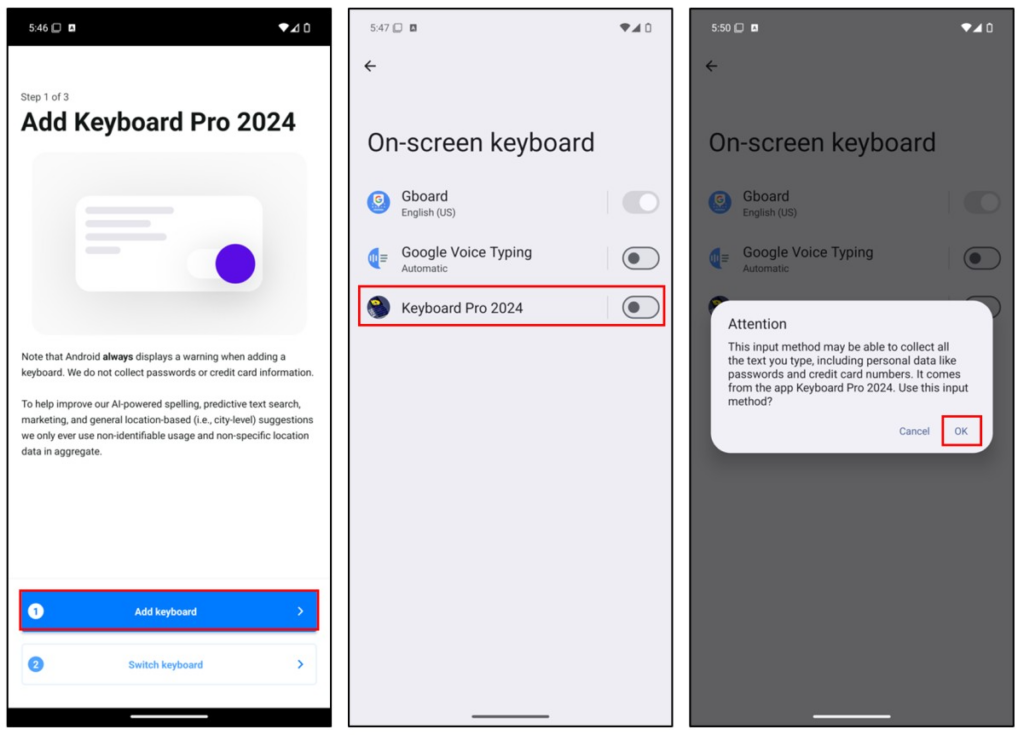
You will see an Android system alert notifying that the input method may have the capability to collect all the text you type. For the purpose of this demonstration, tap the “OK” button to proceed. Then, navigate back to the application and tap the second button to switch the keyboard.
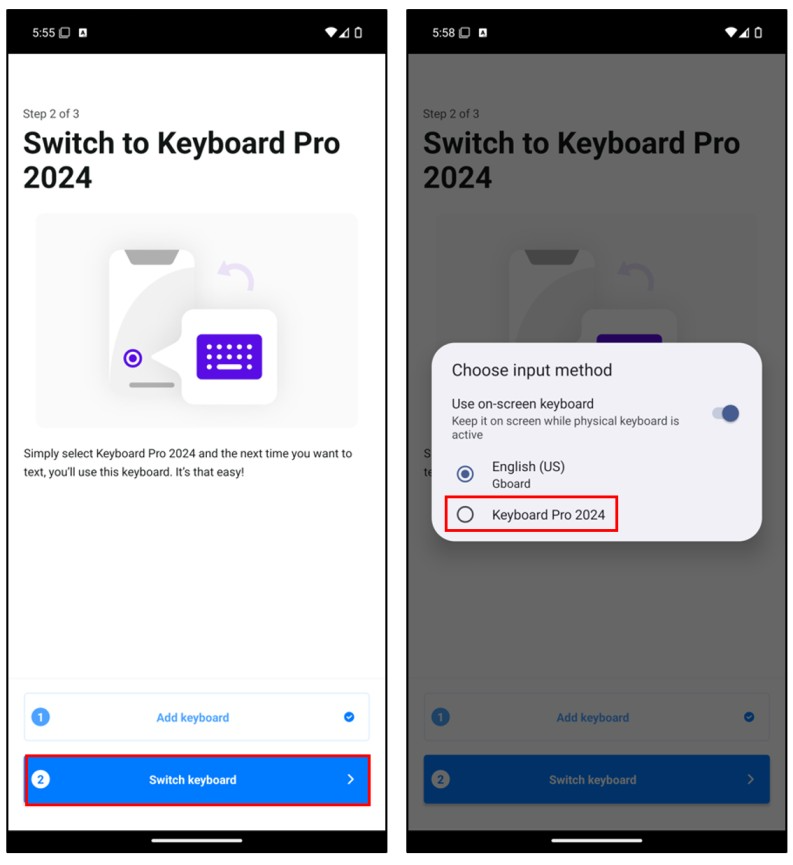
After switching the keyboard, an advertisement will appear in the application. To verify that the Android device has successfully switched to the new keyboard, I navigated to Google and tapped on the search bar. This confirmed that the default keyboard had indeed changed to “Keyboard Pro 2024” as shown below.
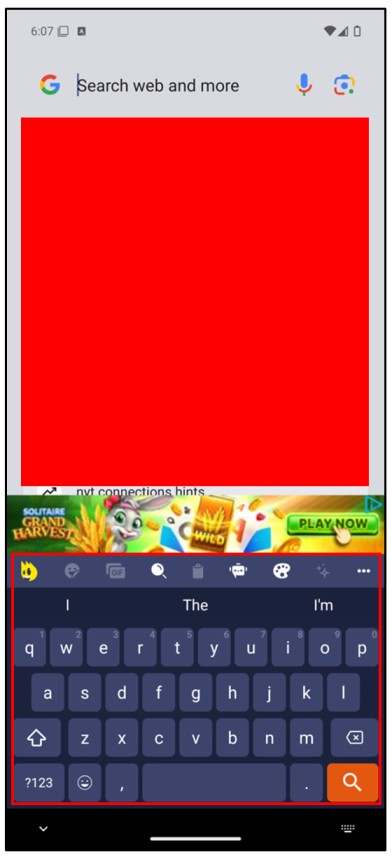
Security in Third-Party Keyboard
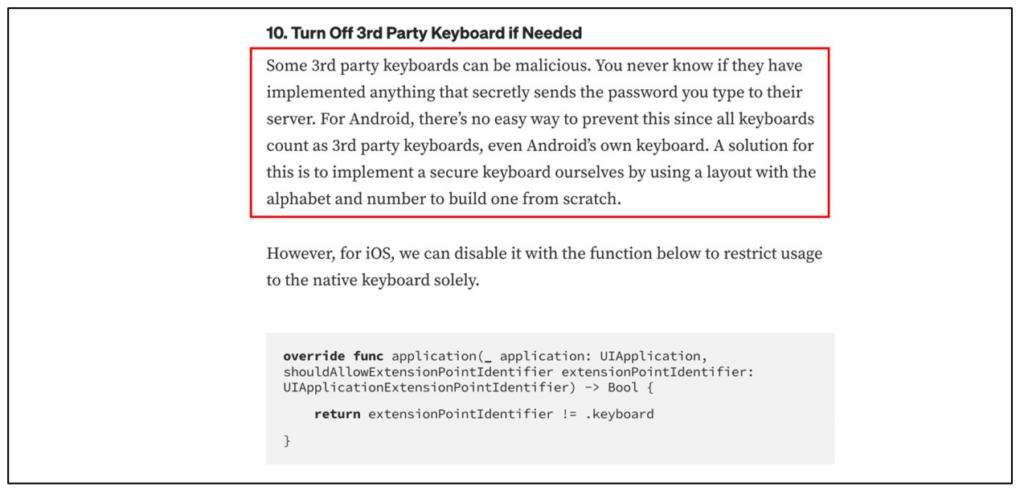
Referencing the Medium article “Mobile Security via Flutter — Ep.2 Strong Device/Strong Pin” (link), section 10 discusses the option to “Turn Off 3rd Party Keyboard if Needed.” While we have already developed a solution for iOS, the Android system presents additional challenges. On Android, all keyboards, including the system keyboard, are treated as third-party keyboards, making them more difficult to detect.
Returning to the “third-party keyboard” (Keyboard Pro 2024), which I previously installed, tapping on the U-turn arrow icon it will show that the application enables the sharing of data about keyboard usage.
Although this application explicitly informs users that data is being collected, using a keyboard not provided by the operating system remains unsafe. This is because attackers can design third-party keyboards specifically to steal information by tracking what users type, such as passwords or PINs.
Detecting a Third-Party Keyboard
For our current solution, McAiden has developed a method to detect third-party keyboards on Android devices using the Kotlin programming language. This approach aims to enhance security by preventing the use of keyboards that are not part of the system, reducing the risk of data theft or malicious activities.
- Accessing Installed Keyboards:
- The method utilizes the
getSystemService(Context.INPUT_METHOD_SERVICE)API to access theInputMethodManager. - This manager provides a way to retrieve details about all installed keyboards (Input Method Editors or IMEs) on the user’s device.
- The method utilizes the
- Identifying the Active Keyboard:
- The
InputMethodManagerallows us to identify the currently active keyboard by fetching its package name or service details.
- The
- Verifying System Keyboards:
- The method employs the
FLAG_SYSTEMflag to determine whether the active keyboard is a system keyboard. FLAG_SYSTEMis used to check if the keyboard originates from the operating system or is preloaded by the device manufacturer. Keyboards that do not meet this criterion are flagged as third-party keyboards.
- The method employs the
- Security Action:
- If the active keyboard is detected as a third-party keyboard, the application can trigger security measures, such as displaying a warning to the user or temporarily disabling sensitive input fields until a trusted keyboard is used.
Here’s an outline of how the logic is implemented in Kotlin:
private fun is3rdKeyboard(): Boolean {
// Get the InputMethodManager system service to access input methods (keyboards)
val im = getSystemService(Context.INPUT_METHOD_SERVICE) as InputMethodManager
// Retrieve the list of all enabled input methods (keyboards) on the device
val list = im.enabledInputMethodList
// Get the ID of the currently active input method (keyboard)
val curr_keyboard_id =
Settings.Secure.getString(
context.contentResolver, // Access system settings content resolver
Settings.Secure.DEFAULT_INPUT_METHOD // Retrieve the default input method (active keyboard)
)
// Loop through the list of enabled input methods
for (imi in list) {
// Check if the current keyboard ID matches the ID of the enabled input method
if (imi.id == curr_keyboard_id) {
// Check the flags of the input method's application info to determine if it's a system app
val flagSystem =
imi.serviceInfo.applicationInfo.flags and ApplicationInfo.FLAG_SYSTEM
// If the FLAG_SYSTEM flag is not set (value is 0), the keyboard is not a system keyboard
return flagSystem == 0
}
}
// If no matching keyboard is found or it is determined to be a system keyboard, return false
return false
}The following figures illustrate a demo application designed to detect whether the user is utilizing a third-party keyboard (a keyboard not pre-installed with the operating system) to input data into the provided field.
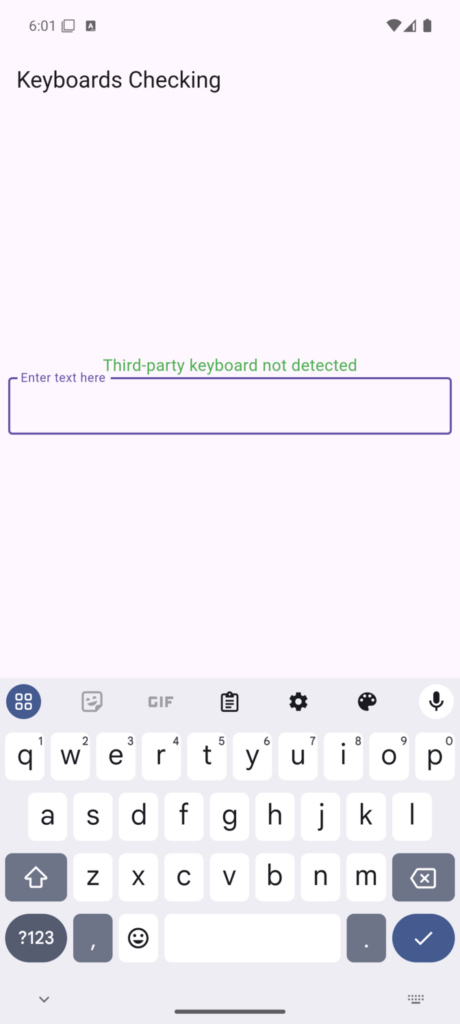
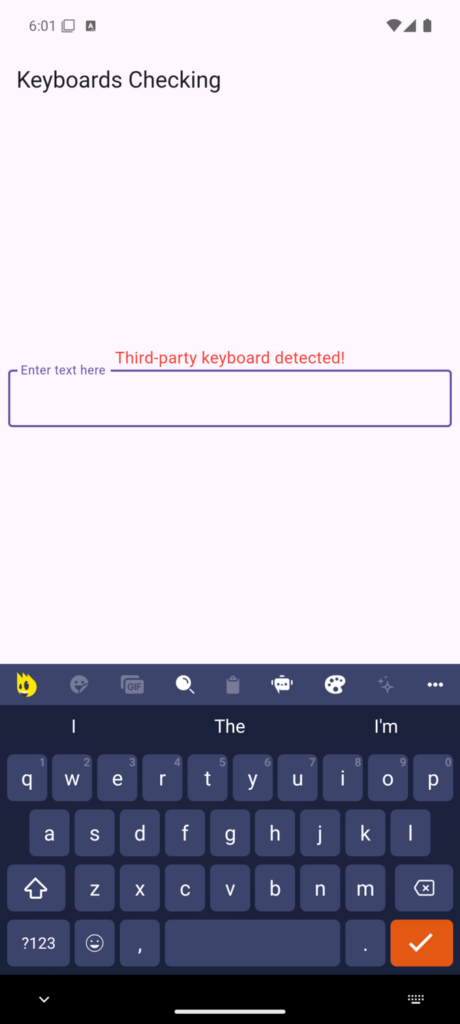
Benefits of This Approach
- Enhanced Security: Prevents users from unknowingly using potentially malicious third-party keyboards.
- Device Compatibility: Works seamlessly with most Android devices by leveraging native APIs.
- Real-Time Monitoring: Continuously verifies the active keyboard, ensuring sensitive data is not exposed during input.
Limitations and Challenges
- Custom ROMs and OEM Keyboards: Some device manufacturers or custom ROMs might modify the behavior of system keyboards, making detection more complex.
Conclusion
This solution leverages built-in Android APIs to identify and restrict third-party keyboards effectively. By integrating this method into applications, developers can significantly improve input security and protect users from potential threats.
More Information found at:



