| Title | AWAE – Brief Course Review for OSWE |
| McAiden Advisory No. | MIDA2025-0007 |
| Service | Web Application Security |
| Publish | 2025-05-21 |
| By | Puwit Yahom |
What is AWAE?
Advanced Web Attacks and Exploitation (AWAE) course is a course offers by Offensive Security which aims toward an understanding of web applications penetration testing. The course shows the learner how to analyze the web application from the ground up ,i.e., obtaining source code to pin-pointing the attack surface.
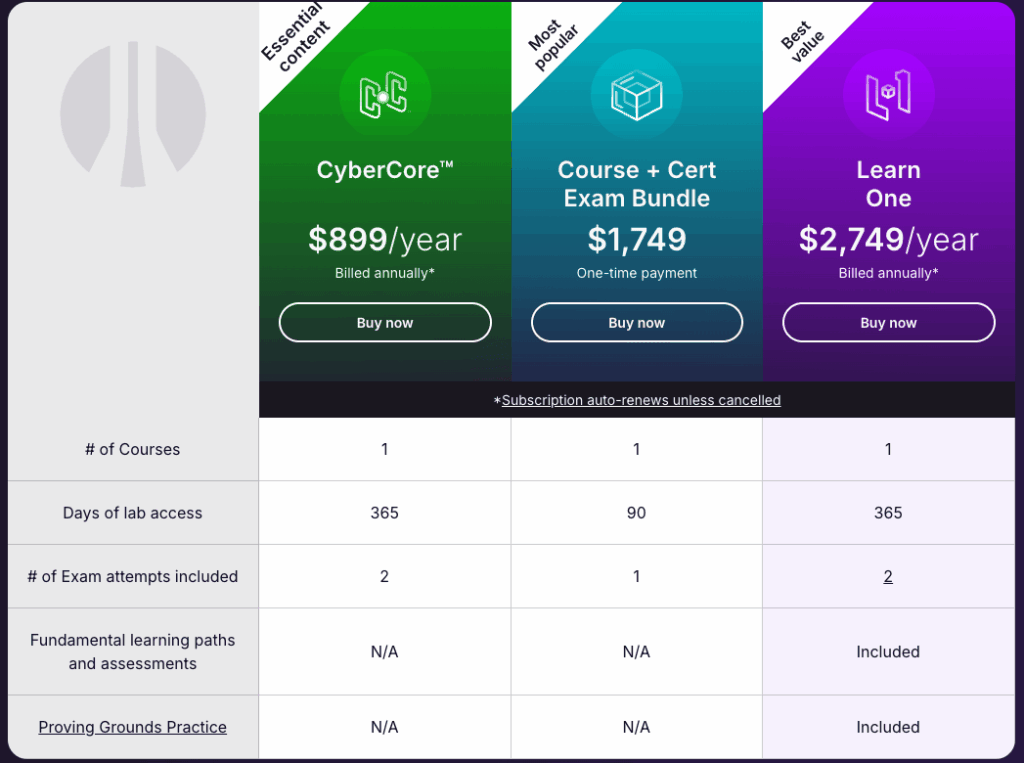
Pricing
For Offsec course in general, the pricing models are divided into 2 types:
- Annually
- CyberCore
- Learn One
- One-time payment
For author, the bundle was kindly given by McAiden on the “One-time payment” option.
P.S. The Proving Grounds Practice is a platform developed by Offsec which contains many vulnerable machines (with writeups) for the penetration testers to hone their skills.
Course Outline
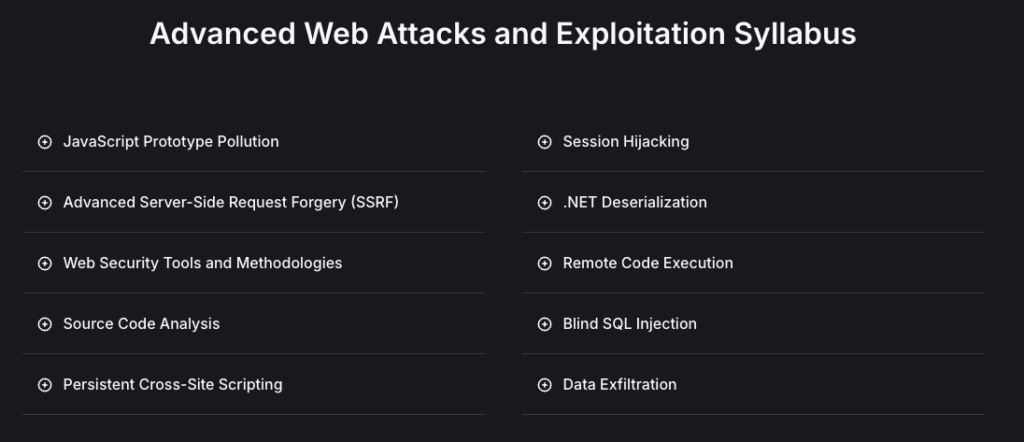
In summary, the AWAE course will teach a learner on how to obtain, debug, and develop an exploit for a web application. Then, the rest will be a real-world case studies from multiple existing vulnerabilities (CVE) from the source code analysis, vulnerability reproduction, and developing a script. The shown case studies also developed different framework (e.g., .NET, Java, PHP) to allow the learner to know how to perform an analysis on each one of them.
Exam
The exam contains 2 target machines with its identical pair (for debugging). Each target contains 2 flags: local.txt and proof.txt.
Main objectives of the exam:
- Bypass Authentication to gain access to Admin page (and obtain the local.txt on the admin page)
- Perform Remote Code Execution to read proof.txt on the server
- Develop a single exploit script that extract local.txt content and/or proof.txt
The passing criteria itself does not require the tester to obtain a reverse shell and does not need to obtain root access.
Exam period
The exam period is 2 whole days (47 hours and 45 minutes) with 1 additional day for reporting.
Exam Report
OffSec has a template report for OSWE. It is recommended to follow all the shown sections in the template report since it will be enough to pass OffSec criteria. It is highly recommended to explain every detail thoroughly. From the methodology of finding a vulnerability to a exploitation steps. In the author case, the report includes both the steps of finding a vulnerable components (analyzing the source code) and proof of concept steps (exploiting the target and writing part of script). Then, provide a full script as required.
Exam announcement
For the author, the report is sent on Monday and the announcement email is sent back on Tuesday (around 24 hours).
Personal Recommendations
In the author opinion, the exam itself is not as difficult as the OSCP since the testers will be given everything one needs (the whole source code) to exploit a web. The thought process for the author is:
- What pages can be accessed?
- Perform a reverse analysis from admin page to unauthorized access
- SQL statements
- Deserialization function
OSWE Certification
After all the hardships, the testers will obtain a OffSec Web Expert (OSWE) Certificate to prove that the testers acquired sufficient skills for web penetration testing. https://credentials.offsec.com/15be4ee4-3c76-45d7-82f2-b776e60cd6df




