| Title | Certificate Pinning Is Not Outdated if You Do It Right |
| McAiden Vulnerability No. | MIDA2025-0002 |
| Product | Android |
| Found | 2025-02-03 |
| By | Nutthanon Thongcharoen (McAiden Consulting Co., Ltd.) Pumipat Korncharornpisuit (McAiden Consulting Co., Ltd.) McAiden Research Lab |
On July 29, 2024, Cloudflare published a blog post titled “Avoiding downtime: modern alternatives to outdated certificate pinning practices” (https://blog.cloudflare.com/why-certificate-pinning-is-outdated/), arguing that certificate pinning is a relic of the past. The article raises valid concerns such as the risk of app downtime during certificate rotations and the complexity of managing pinned certificates. However, certificate pinning is not inherently outdated; it is outdated only when implemented poorly. When done correctly, it remains a powerful technique for enhancing app security, ensuring that applications communicate with the correct server, especially for high-risk industries like banking, healthcare, or government services.
In this article, I will explain why certificate pinning still matters and how to avoid downtime when implementing it. The discussion is divided into three parts:
SSL Certificates
SSL Certificates have become a widespread tool for securing web and mobile applications. To launch a new certificate, it will have a key pair consisting of a private key and a public key. There will be a range of components in a certificate including a subject, an issuer, a public key, and others.
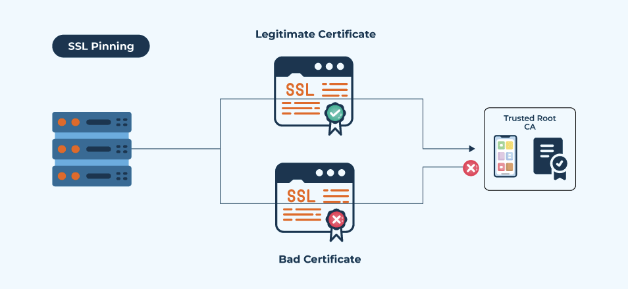
Today, we implement SSL Certificates in mobile applications using a technique known as certificate pinning. This security method involves embedding the server’s certificate or public key into the application. This approach is particularly crucial for applications that require high security, such as:
- Mobile Banking application
- Healthcare systems
- Government services
Certificate pinning ensures that an application only trusts a specific certificate or public key, preventing attackers from using fraud certificates to intercept traffic and ensures an application only communicates with servers holding specific, pre-approved certificates.
Certificate Chain of Trust
To understand the problem, we must first examine the Certificate Chain of Trust. This chain consists of three tiers, each playing a distinct role in security and stability:
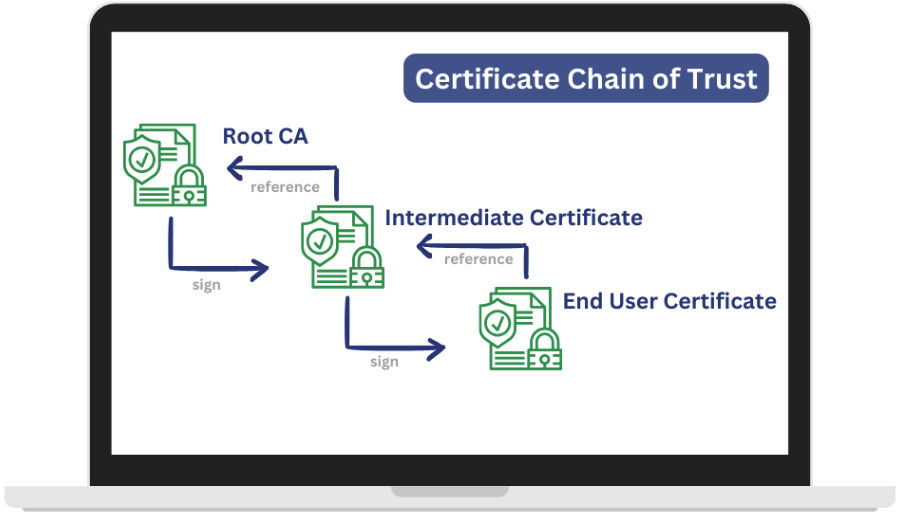
Root Certificate
The root certificate sits at the top of the chain and is self-signed by a Certificate Authority (CA). These certificates have long lifespans (over 10 years). and are strictly controlled by CAs. They are rarely replaced, making it highly stable but risky to pin directly.
Intermediate Certificate
Intermediate certificates act as a bridge between the root and leaf certificates. They are issued by the root CA and have shorter lifespans (typically 5-10 years). These certificates are used to sign leaf certificates, isolating the root CA from direct exposure.
Leaf Certificate
Leaf certificate is the end-entity certificate issued to a specific domain (for instance: example.com). These certificates are short-lived, expiring every 90 days or less. Pinning leaf certificates is where most developers go wrong because it rotates frequently, Applications that pin them risk breaking and get downtime when the certificate expires.
The Problem Is Not Pinning—It is What You Pin
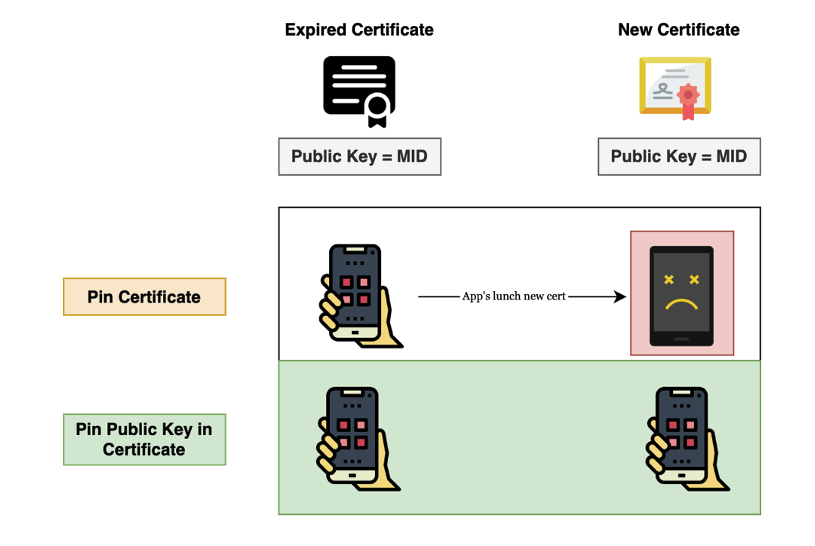
From the Cloudflare article, the primary criticism of certificate pinning centers on its level of Certificate Chain of Trust. Application that directly pins the leaf certificate often break, since leaf certificate typically expire every 90 days. This creates downtime of application in case an application is not updated with a new certificate when its older one is near its expiration date, it stops working.
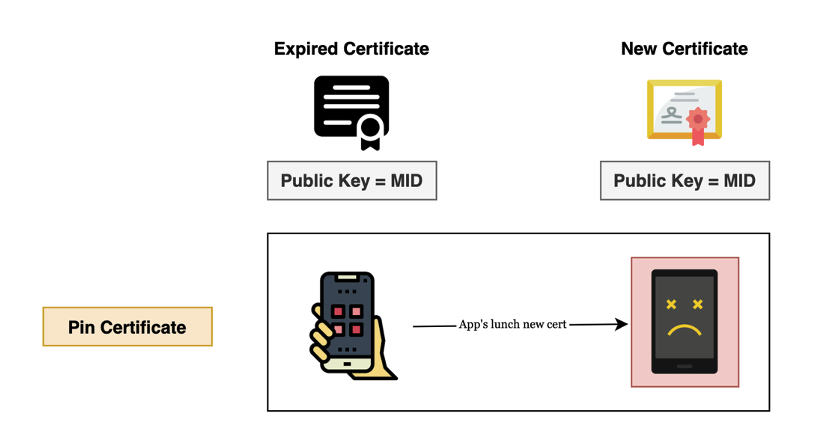
But its problem comes in its use, not in its principle. Developers will not have to pin leaf certificates but will have to pin public keys that sit in the certificate. With such an approach, even when left certificates change, an application can go through with no downtime. After a leaf certificate expires, an Intermediate CA will issue new leaf certificates with the same public key, and an application will run with no downtime.
Summary
Cloudflare’s blog raises concerns about certificate pinning, citing risks like downtime and complexity during certificate rotations. However, the issue lies in implementation—pinning public keys instead of leaf certificates avoids disruptions, as public keys remain consistent across renewals. Properly implemented, certificate pinning ensures stability and security, making it essential for high-security applications like banking, healthcare, and government services.
More Information can be found at:
- https://blog.cloudflare.com/why-certificate-pinning-is-outdated/
- https://www.cloudflare.com/learning/ssl/what-is-ssl/
- https://sslinsights.com/what-is-the-certificate-chain-of-trust/
- https://owasp.org/www-community/controls/Certificate_and_Public_Key_Pinning
- https://www.ssl.com/blogs/what-is-certificate-pinning/



